Von Anfang an haben wir eng mit der Sicherheits-Community zusammengearbeitet. Version bringt neue Funktionen, darunter ein HTML5-basiertes Interface sowie die Unterstützung für Androi iOS und Windows 8. Instea you can install it on only one computer and test as many computers as you would like. Die Reports können in verschiedenen. Nessus Professional kaufen.

In your scan , you can choose to view all vulnerabilities found by the scan, or vulnerabilities found on a specific host. Vulnerabilities are instances of a potential security issue found by a plugin. Installation files for Windows typically have the. It also shows to generate a nessus scan report for your scan.
Choose business IT software and services with confidence. As a vulnerability analyst by trade, I spend a lot of time using vulnerability scanners. Users can schedule scans across multiple scanners , use wizards to easily and quickly create policies. Corrective action may not be possible or is not required.
Features of this tool include local and remote security checks. OpenVAS is a full-featured vulnerability scanner. Tenable Network Security. Its capabilities include unauthenticated testing, authenticated testing, various high level and low level Internet and industrial protocols, performance tuning for large-scale scans and a powerful internal programming language to implement any type of vulnerability test.
ISO is currently in the process of testing this and looking for potential workarounds. There is a wide range of scanners that are available in the market. Manage all aspects of a security vulnerability management system from web based dashboards. This category of tools is. Now we learn how to scan machines.
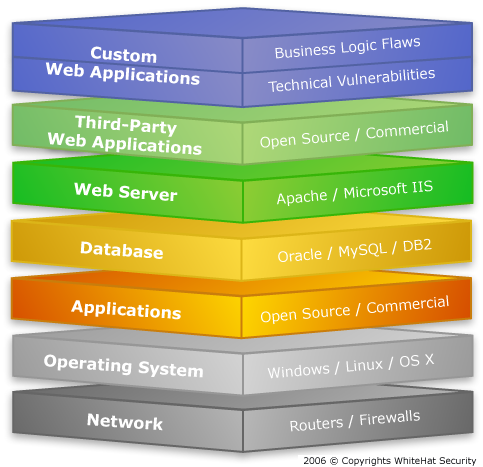
Therefore, it is widely used in multiple organizations. Also tests Nmap NSE scripts. These applications are designed to identify vulnerabilities that may exist within a target by comparing these hosts against a. Industry standard vulnerability , configuration, and compliance assessment. Unique protection for BYO Clou and SCADA systems.
Continuous Monitoring - Streamline Audits, Incidents, and Investigatio. It only takes one misconfigured device or missing patch for hackers to infiltrate your network. The same functionalities exist on Mac OS X, Windows, and Linux. I have come across an issue as an example of where we see a vulnerability with your product.
Identifying vulnerabilities is the first step towards securing your environment. Microsoft Windows Unquote. Scans can be composed of. It helps to easily identify and fix vulnerabilities – including software flaws, missing patches, malware, and misconfigurations across a variety of operating systems, devices and applications.
In this tutorial, we are going to learn how.
Keine Kommentare:
Kommentar veröffentlichen
Hinweis: Nur ein Mitglied dieses Blogs kann Kommentare posten.